PeckShield blockchain security firm shared a warning concerning potential vulnerabilities within the Aave Protocol’s Earning Farm. The company shared distressing information paired with a transaction screenshot, suggesting that the Earn Farm on Aave might be under the threat of an exploit known as a “reentrancy hack.”
🚨#PeckShieldAlert ~$287K #Ethereum pic.twitter.com/TOQ9oSzcGN
— PeckShield Inc. (@peckshield) August 9, 2023
A reentrancy hack (or reentrancy attack) occurs when an attacker can breach a function and, while the function is still executing, call back into that same function, essentially allowing them to withdraw funds repeatedly before the original function call is completed. It is a dangerous exploit as it can quickly drain funds, often leaving projects and investors with significant losses before they even realize an attack is underway.
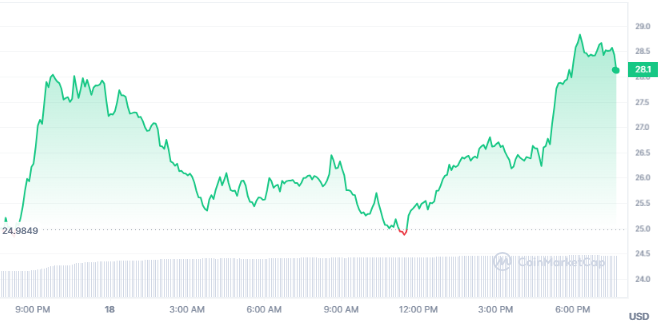
As it stands, the damage has already reached a concerning figure. The security breach has led to a heist of approximately $287,000. This unsettling news underscores the pressing need for immediate action from anyone interacting with the Aave Protocol’s Earning Farm.
How to avoid further losses?
To ensure the safety of your funds and operations, users should revoke permissions. This step will prevent any further unauthorized access or malicious activities from taking place on your accounts.
As always, maintain vigilance. Avoid signing any transaction that appears dubious or out of place. In times of security breaches, malevolent actors may attempt to capitalize on the chaos, introducing further exploits or phishing attempts.
Keep an eye on official announcements from Aave, Earning Farm and PeckShield. As more details about the breach unfold, it is crucial to be informed of any developments or corrective measures that need to be taken.
The DeFi space, while filled with opportunities, is not devoid of scams, exploits and malicious actors. Projects built on as well-established protocols as Aave can fall prey to the continually evolving tactics of malicious entities.
Sourced from cryptonews.net.